By: Larry Barker
Having the ability to determine what the current Effective Access is across an IBM Notes and Domino application base is critical for both day-to-day IT operations and alignment with many auditory requirements and frameworks.
In the case of day-to-day business, IT departments face many challenges specific to Notes application access and availability management. They may need to perform routine changes or processes involved with general security enforcement, or “housekeeping” duties that could require up-to-date security reporting. With regard to staffing, IT departments need to perform processes like the change management of leavers, joiners, and movers across multiple servers, domains, and applications.
We’re increasingly hearing that our customers need the ability to meet auditory requirements of ITSM related frameworks and legislation. These requirements necessitate capturing and reporting on the true security access of users and groups across the environment. As an example, planning and/or enabling controlled processes around the design, transition, and management of new and existing applications into production all require a solid understanding of any resulting Effective Access in order to ensure appropriate end-user application access.
Other than day-to-day IT operations and alignment with auditory requirements, there are many projects that require Notes Effective Access information. Migrating to a new platform and needing to model or recreate your application security access levels is one example. Another example is the desire to kick off a NAB cleanup initiative to gain control of Notes Access Control Lists that suffer from complicated nested and circular group entries being applied over the years without a true understanding of their overall effect on application security.
Manually Investigating Notes Effective Access Is Tedious Work.
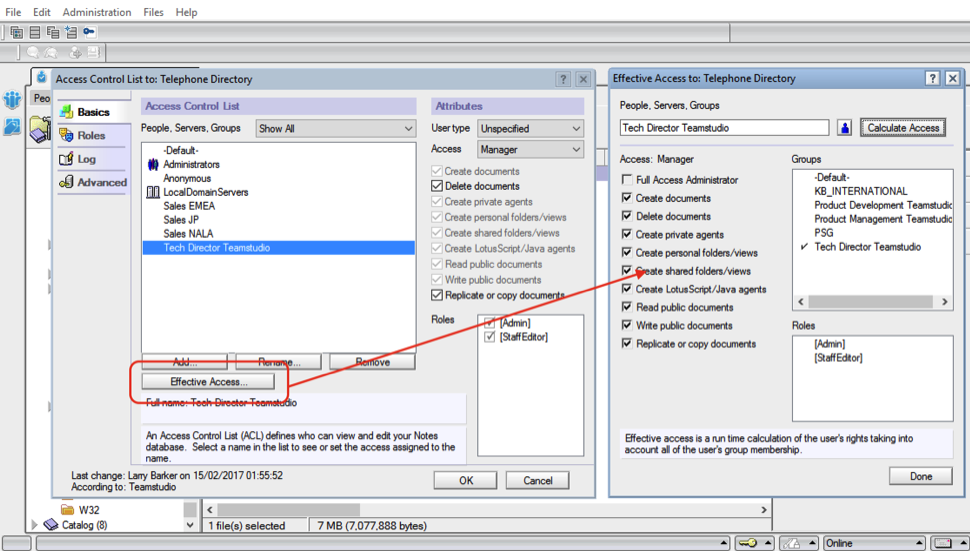
Whatever your project or need, you’ll likely find that there are not any great features within Domino to enable you to consolidate, interpret, and act upon Effective Access data out-of-the-box without significant effort and resource expenditure. Those familiar with Domino administration will be very familiar with the usual per user/group/application approach currently employed using both the Effective Access calculation feature in the Notes ACL Management Panel (see Fig. 1), or the information provided via the taskbar security button.
(Fig. 1) The Effective Access calculation feature in the Notes ACL Management Panel
But what if you need to go a step further and truly understand your Effective Access landscape? You may be able to write an agent to scrape and collect portions of the needed data from your Domino logs, but being able to extrapolate all nested groups and explicit ACL entries across all applications, servers, and mixed domains will be very complicated. You’ll run across several challenges including parsing through nested and circular group ACL entries, conflicts between explicit and group sourced permissions, as well as duplicate entries across domains.
Understanding Notes Effective Access Is Easy with Teamstudio Adviser.
Teamstudio Adviser allows you to capture, analyze, and understand your Effective Access across not only multiple applications but also servers and differing domains. This capability will enable you to meet the requirements of the previously mentioned scenarios.
You may begin by understanding what the Effective Access is to a specific application by opening the Catalog module within Adviser and searching for your application. Each Domino application will have an Effective Access panel presenting you with the overall end user and group access (see Fig. 2) as well as several other DB properties including their ACL. Basically, you’re presented with the actual end user access levels after all nested and explicit entries are taken into consideration.
(Fig. 2) Teamstudio Adviser showing overall end user and group access for a Domino application
This gives us the Effective Access levels for all users and groups against a specific application. But what if we want to understand what an end user’s or group’s Effective Access level is against multiple DBs, whether it’s within a single server or multiple domains, etc.? In this case, you may simply open within Adviser the specific user or group record displaying the calculated Effective Access against all cataloged databases (see Fig. 3). This will show you the selected user’s or group’s Effective Access against every application.
(Fig. 3) Teamstudio Adviser displaying a selected user’s or group’s Effective Access against every application in the environment
So, not only can we see the true access levels for all users of an application and all applications to which a user has access, but we can also see all groups in which a user is a member. This is displayed for both groups where the user is explicitly listed as well as any nested groups they may be listed within (see Fig. 4). From the figure, you may also notice you have the option to list only groups where the entry is explicitly listed, or list also the nested groups to which they have also been added.
(Fig. 4) Teamstudio Adviser showing all groups in which a user is a member
Notes Effective Access is only one subset of information Adviser is able to produce. If you have other requirements where you would like to take into consideration different aspects such as application usage or design complexity, Adviser also contains specific modules that provide that information. For more details on Adviser’s Effective Access feature or its other modules, please feel free to reach out to us for more information or a demonstration.
-Larry Barker, Technical Director, Teamstudio